Retail being a highly competitive industry is always at the forefront of technological innovations. With the rising focus on customer satisfaction and efficient business processes, adopting the latest technological innovations is the only way to stay ahead in the game. With the more recent emphasis on omnichannel, customer experience, and ever-growing competition as well as demand, retail has had to focus not on one aspect but, on several including branding, e-commerce, customer service, product deliveries and so on..
The Internet of Things holds the potential of driving such truly connected, omnichannel experiences. It isn’t a far stretch to say that the way consumers now make their purchase decisions has completely been transformed and for retailers, IoT provides to them an insight on making smarter, more informed business decisions by knowing their consumers better, gauging performance of their products, and leveraging ways to make existing customer experiences’ smoother and acquiring new ones.
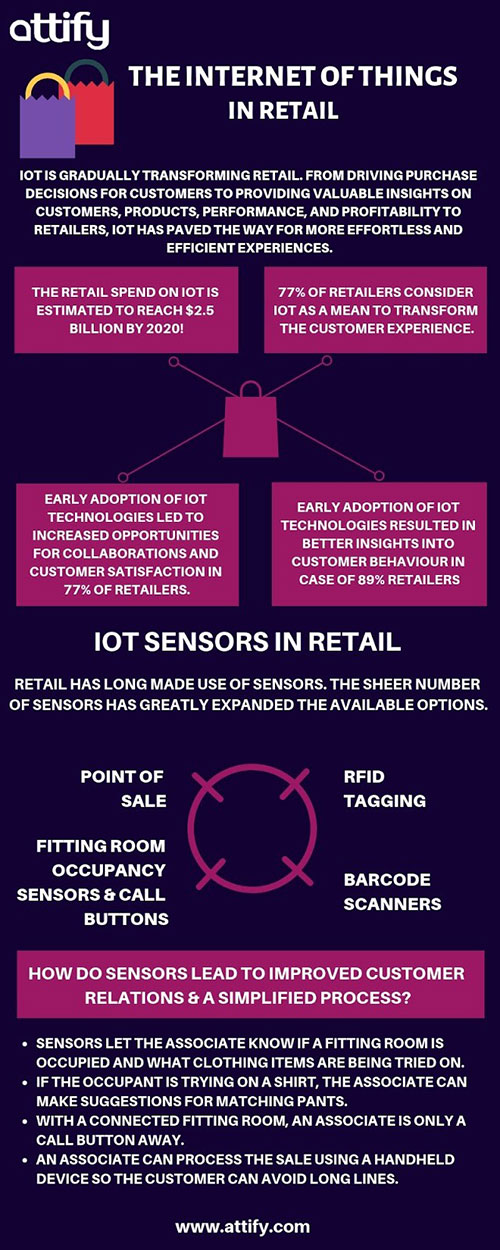
Amongst many things, IoT has now made possible a world where retailers roll out smart shelves, robotic sales assistants, and implement smart sensors, RFID tags for monitoring goods. Retailers deploy IoT enabled technologies for improved efficiency in terms of - monitoring and maintenance, location-based services, networking between various IoT devices, and customer devices over WiFi.
While IoT promises all that has been mentioned above, it still is far from being 100% secure. The rising demand for IoT technologies globally has invariably created more pressure on the device manufacturers leading them to compromise on quality. With the number of connected devices increasing throughout the various verticals along the supply chain, the retail sector is now at a heightened state of exposure to security breaches.
According to a survey by PwC in 2017, the retail and consumer sector suffers an average of 4,000 information security threats every year. Additionally, the report revealed that 16% of all the organizations surveyed suffered losses of over $1 million because of incidents related to information security.
Information is a valuable commodity and with the retail sector being the pioneer in the case of most money-related exchanges, it makes up for 8% of all data breaches.
Now that we have established what the scenario of retail sector with respect to the Internet of Things is, let us delve further into the various security threats or challenges that a modern-day retailer needs to be aware of and the possible solutions in order to cope up with each one of them.
Security Challenges
Network Infiltration
While everyone would easily agree that securing IoT enabled devices is a priority to safeguard themselves against security breaches but, what’s equally important is the network or the gateways that these devices are functioning on. With cyber criminals finding numerous ways to exploit company networks, there has been a myriad of research into securing networks from outside control and manipulation. The complementary issue is the interplay between the network structure and framework execution.
Problem: With the high volume of payment card information and personally identifiable information (PII) living on servers, on the cloud, and across the network, it is no surprise that retail consumers are an appealing focus for would-be criminals and perpetrators of fraud. Cybersecurity that gives layered protection to networks, systems, and information within the cyberspace is a critical issue for all.
Solution: Businesses need to be extra vigilant regarding consumer information protection and employ an in-depth cybersecurity strategy to easily thwart even the largest of attacks and perform regular penetration tests to protect its infrastructure. Taking some simpler steps like using a WIPS (Wireless Intrusion Prevention System), an antivirus software, and end-to-end encryption are some common measures that can help strengthen network security. Ensuring a fully managed network by granting role based access and segmenting the network (isolating sensitive information) is also extremely important for maintaining network security.
DDoS Attacks
According to the 2015 Verizon’s Data Breach Investigations Report (DBIR), DDoS attacks are the most common form of attack within the retail industry. In 2018, with the increasing number of retailers deploying IoT products to streamline a wide range of tasks, from inventory administration to vehicle tracking, the risks of such attacks have significantly gone up.
Problem: The advancement of the Internet of Things has led to the creation of innovative devices like smart shelves, RFID trackers, and perishable goods sensors. Consequently, embrace the possibility that these IoT devices can be infected with botnets by exploiting common vulnerabilities, which are then used to perform DDoS attacks on the websites. A DDos attack takes control over a large number of computers and the network/server they’re being operated on, ultimately rendering a service (such as an e-commerce website) slow and in some cases, even completely unresponsive.
Solution: Retailers should work in close collaboration with IoT manufacturers to ensure that they manufacture IoT devices that have robust security features which cybercriminals cannot easily penetrate. One of the most important safety mechanisms to prevent any cyber attack is to monitor your network for any suspicious activity. A sudden slowdown in network performance could be an alarming factor. Another option in the event of a DDoS attack is to set up a cloud-based anti-DDoS solution so that any form of malicious traffic can be diverted.
Ransomware
Over the recent years, Ransomware has become one of the biggest menaces for all businesses across the globe. According to the NTT Security Report, 15% of Ransomware attacks were targeted at retail.
Problem: Malware attacks continue to become more sophisticated and unforgivingly brutal. Crypto-ransomware that basically scrambles records and renders them garbled without a decoding key has turned out to be progressively common as of late. Organizations pay every one of these ransoms since they don't have legitimate backups of their security systems.
Solution: Therefore, as a first step towards protecting their network and systems, retailers must embrace the idea of backing up their systems and applying the latest patches on a regular basis. It is vital for companies to regularly scan their IT infrastructure for vulnerabilities, misconfigurations, viruses, and malware at both the network and application level. Other than the above mentioned strategies, retailers should also ensure that data access roles be defined so that, only a select number of employees have access and that they regularly change their passwords.

Social-engineered attacks
It's sufficiently troublesome for an organization to confirm the security of its own computing environment when it has various conveyance centres, stores, online catalogues and corporate workplaces. While retailers continue to spend huge amounts of money on various softwares in order to safeguard against cyber attacks, do they consider their own employees when it comes to assessing the weak links? Social engineering attacks such as phishing emails are till date, a hugely popular method used by attackers. A survey conducted by computerweekly.com, revealed that more than one in 10 employees fall for social engineering attacks.
Problem: Various research studies have revealed that as many as 25% of employees have clicked on phishing links sent to them via email or social networks. Once an attacker gains access to one of the systems in the organisation, he can move laterally within the network to attack and assume control over the entire infrastructure. However, this isn’t surprising given the lack of training facilities with regard to cybersecurity for employees at most organisations.
Solution: Consequently, retailers must develop programs to educate their employees, reinforce security awareness messages among their staff and customers especially in this era, where human-focused attacks like phishing and social engineering are at their peak. Schedule a private IoT Security Training session for your organisation today.
With cybercriminals adopting newer and more advanced ways to wage war, the next generation retailer must focus on the above aspects when it comes to getting ready to meet the cybersecurity challenges for 2018. These security challenges can be mitigated by recognizing and understanding the most vulnerable points which are often the cybercriminals’ first point of attack during an attempt to gain access to a system. In order to better secure their systems, retailers can also partner with cyber-security experts and other knowledgeable and resourceful partners to handle these challenges.
About Attify
Attify provides tailored Penetration Testing Services and Complete Security Assessments of your IoT Devices through a unique offering of Attacker Simulated Exploitation for IoT solutions.
Also, get started with our Hands-On Offensive IoT Exploitation Training, conducted by the best in class experts. Learn Firmware Reverse Engineering, Embedded Device Hacking, Binary Exploitation, Radio - BLE, ZigBee exploitation and more.






